you can encrypt in 4 method
- server side encryption (SSE)
- Server-Side Encryption with Amazon S3-Managed Keys (SSE-S3) – Enabled by default Encrypts S3 objects using keys handled manege and owned by AWS
- Server-side Encryption with KMS Keys Stored in AWS KMS (SSE-KMS) Leverage AWS Key Management Service (AWS KMS) to manage encryption keys
- Server-Side Encryption with Customer-Provide Keys (SSE-C) When you want to manage your own encryption keys
Client-side Encryption
- Server-Side Encryption with Amazon S3-Managed Keys (SSE-S3)
we don’t have access to this key Encryption using a key handled managed and own by AWS
object is encrypted server-side
AES-256 is the encryption type
must set header “x-amz-server-side-encryption”:”AES256″
Enabled by default for new buckets & new objects
- Server-side Encryption with KMS Keys Stored in AWS KMS (SSE-KMS) Encryption is handled and manages by AWS KMS (Key Management Service) KMS advantages : user control + audit key usage using CloudTrail object is encrypted server side must set header “x-amz-server-side-encryption”:aws:Kms” SSE-KMS Limitation when you upload it calls the GenerateDateKey KMS API When you download it calls the Decrypt KMS API count towars the kms quota per second
(5500, 10000, 30000 req/s based on region) you can request a quota increase using the Service Quotas Console - Server-Side Encryption with Customer-Provide Keys (SSE-C) the encryption using keys fully managed by the customer outside of AWS Amazon S3 does not store the encryption key you provide https must be used encryption key must provided in http headers for every http request made
- Client-side Encryption Use Client libraries such as Amazon S3 Client-Side Encryption Library Client must encrypt data themselves before sending to Amazon S3 Clients must decrypt data themselves when retrieving from Amazon S3 Customer fully manages the keys and encryption cycle
- Amazon S3 Encryption in transit (SSL/TLS) Encryption in flight is also called SSL/TLS Amazon S3 exposes two endpoints HTTP endpoint – non encrypted https end point encryption in fligth https is recomended https is mandatory for SSE-C most clients would use the https endpoint by default Force encryption in transit bucket policy we put “aws:SecureTransport” : “false”
Example:
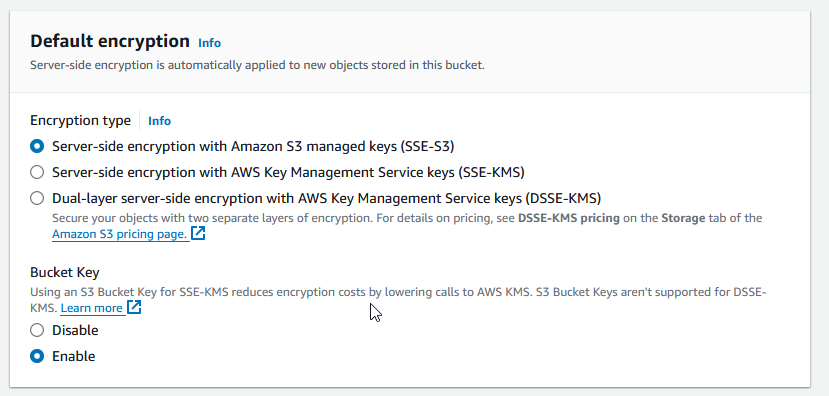
When we create a bucket we can choose the encryption type this time we choose default encryption
Server-side encryption with Amazon S3 managed keys (SSE-S3)
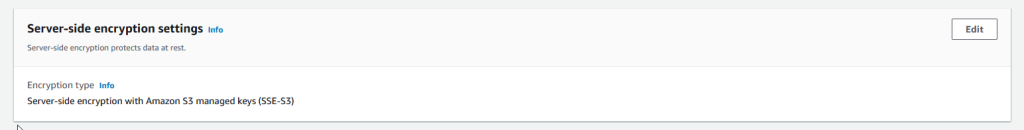
after create the bucket and load a file we can modify the encryption we go to the file go to server-side encryption settings
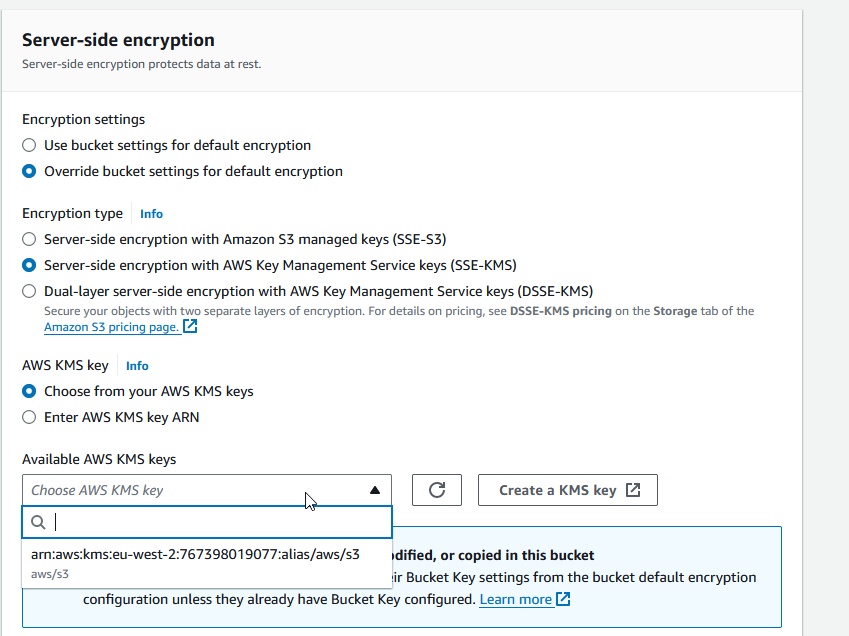
then a windows appear , we can change the encryption this time we choose Server-side Encryption with KMS Keys Stored in AWS KMS (SSE-KMS)
then we choose : choose from your AWS KMS Keys from AWS KMS Key section
Leave a Reply
You must be logged in to post a comment.